|
Blocking USB Threats
by Ralph Moore
January 5, 2022
Factory threats are escalating at a staggering rate. Honeywell has written a helpful report (Ref. 1) on how USB devices are being used to circumvent the air gap that protects most factories. This is becoming a serious industrial cybersecurity problem. One type of USB device is specifically designed to inject a trojan horse into a factory controller. The most dangerous hackers now belong to syndicates, wherein, like the Mafia, each actor has a specialty (e.g. safe cracker, get-away driver, etc.) A syndicate actor that I will refer to as the cracker, starts the attack.
For example, a cracker hires in as a janitor for a factory that is targeted by his syndicate. The first day on the job, he sweeps around the factory floor looking for the targeted factory controller. When he finds it, he sweeps up to it, surreptitiously takes a USB attack device from his pocket, plugs it into the controller, then sweeps away. Later he sweeps back, removes the device, and finishes his shift. The next day he fails to show up to work, never to be seen again.
The trojan horse remains idle for a few days, then goes into action. It spreads malware through-out the factory system. Then it establishes C2 (Command and Control) contact with syndicate headquarters and it and its progeny lie low until orders are received from headquarters. In practice, there are many kinds of orders that might be issued depending upon the syndicate's objectives for this target (e.g. shutting down the factory until a ransom is paid, stealing data on how to manufacture certain parts, etc.). Meanwhile the invaders go undetected.
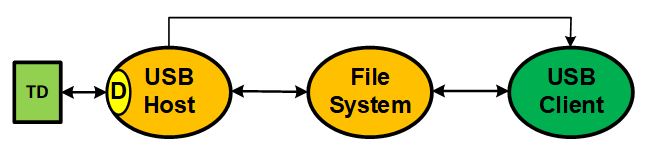
The figure above shows the controller firmware structure that would exist under SecureSMX, our next generation security RTOS for microcontrollers. Ellipses represent isolated partitions and the lines between ellipses represent portals. The portals act like bridges over moats surrounding partitions. There are two types of portals:
- A free message portal accepts one protected message at a time.
- A tunnel portal permits multiblock transfers of large amounts of data.
TD, above, is a USB thumb drive (real or not), which connects to the USB device driver, D. The USB host stack and the device driver are in an isolated partition. The file system and the USB client application are also in isolated partitions. When the USB thumb drive is plugged into the factory controller, a connect message is sent to the USB client via its free message portal. This causes the client to initiate a file transfer via a tunnel portal in the file system partition. The file system, in turn, initiates a file transfer via the mass storage tunnel portal in the USB Host partition. The USB client expects to receive information from the USB thumb drive telling it what to do, but that does not happen.
When the trojan horse is called into action, whatever partition it is in, the first time it steps outside of that partition or attempts a prohibited operation (e.g. executing code from RAM), it will trigger an MMF (Memory Manage Fault) alarm, the partition will be shut down, and OPCON will be notified. Probably an OPCON engineer will come out to inspect the factory controller, then reboot it, thus evicting the trojan horse and resuming normal operation. So the factory escapes serious damage!
Another type of attack that the Honeywell report describes is where malware has been embedded into what appears to be a normal file on a thumb drive. The thumb drive is plugged into the factory controller by an operator to start making the next part. Honeywell has developed a filter, ironically called "Forge SMX", which detects bad files and rejects them.
The above figure shows how this filter can be put into its own partition and placed between the file system and the client partitions. This is done without changing any code in either of them, which is an advantage of communicating via portals. Honeywell says that Forge SMX is exceptionally effective, which is good news for factory owners. Thus the factory dodges yet another bullet!
For more information on the USB Threat and on how to improve factory security and embedded device security through partitioning, see:
- Industrial Cybersecurity USB Threat Report 2021, Honeywell International Inc. 6/21
- Achieving Full MCU Partition Isolation, Part 1: Basics, Ralph Moore, 6/18/21
Ralph Moore is a graduate of Caltech. He and a partner started Micro Digital Inc. in 1975 as one of the first microprocessor design services. Now Ralph is primarily the Company RTOS innovator. He does all functions including product definition, architecture, design, coding, debugging, documenting, and assisting customers. Ralph's current focus is to improve the security of IoT and embedded devices through firmware partitioning. He believes that it is the most practical approach to achieving acceptable security for devices connected to networks and to the Cloud.
Copyright © 2022 Micro Digital, Inc. All rights reserved.
|